20. Components » BGP Connector¶
Wanguard sends and withdraws BGP announcements (aka advertisements or routing updates) in the following cases:
► To protect the network by announcing DDoS’ed destinations to the upstream provider(s) using a special BGP community. In less than a second, the undesirable traffic is dropped before it enters the protected network because the BGP peers will no longer route the attacked addresses, making them effectively null-routed. This network protection technique is called RTBH (Remote Triggered Black Hole), blackhole routing or null-routing► To re-route attacked destinations through servers running Wanguard Filter, which analyzes the traffic, rejects the bad packets, and re-injects the cleaned traffic back into the network. This network protection technique is called traffic scrubbing, side filtering, sinkhole routing, or clean pipe► To leverage BGP Flowspec for mitigation and/or traffic diversion. Flowspec enables mitigation directly on the edge router and offers a much more granular mechanism for matching traffic. Some of the match fields supported by BGP Flowspec: Destination Address, Source Address, IP Protocol, Source Port, Destination Port, ICMP Code, TCP Flags► To announce the attacking IP in BGP when S/RTBH is available► Console users can null-route traffic manually, e.g., to block access to a specific IP address for abuses or legal requirements► Console users can divert traffic manually, e.g., to inspect packets for troubleshooting purposes
- The following backends are handling the communication with the BGP-enabled routers:
- ■ Quagga and FRR provide a mature and widely used BGP daemon that closely resembles existing closed-source platforms like Cisco IOS. This is the recommended backend if the router doesn’t support BGP Flowspec■ ExaBGP is a tool typically used outside the data plane to do path manipulation on a BGP network that may be composed of closed-source components. ExaBGP supports newer technologies such as BGP Flowspec■ GoBGP is an implementation of the BGP protocol in the Go language. It is faster and much easier to use than exabgp, but it does not have some of exabgp’s features such as flowspec redirect ip
To add a BGP Connector, click the [+] button from the title bar of the Configuration » Components panel. To modify an existing BGP Connector, go to Configuration » Components and click its name.
20.1. GoBGP Connector¶
Before you add a GoBGP Connector, make sure you have a fully-functional gobgp. If you do not, jump to the GoBGP installation section. You can have a single gobgp and many GoBGP Connectors using it, which is useful if you need to send announcements with different parameters, e.g., when using multiple communities.
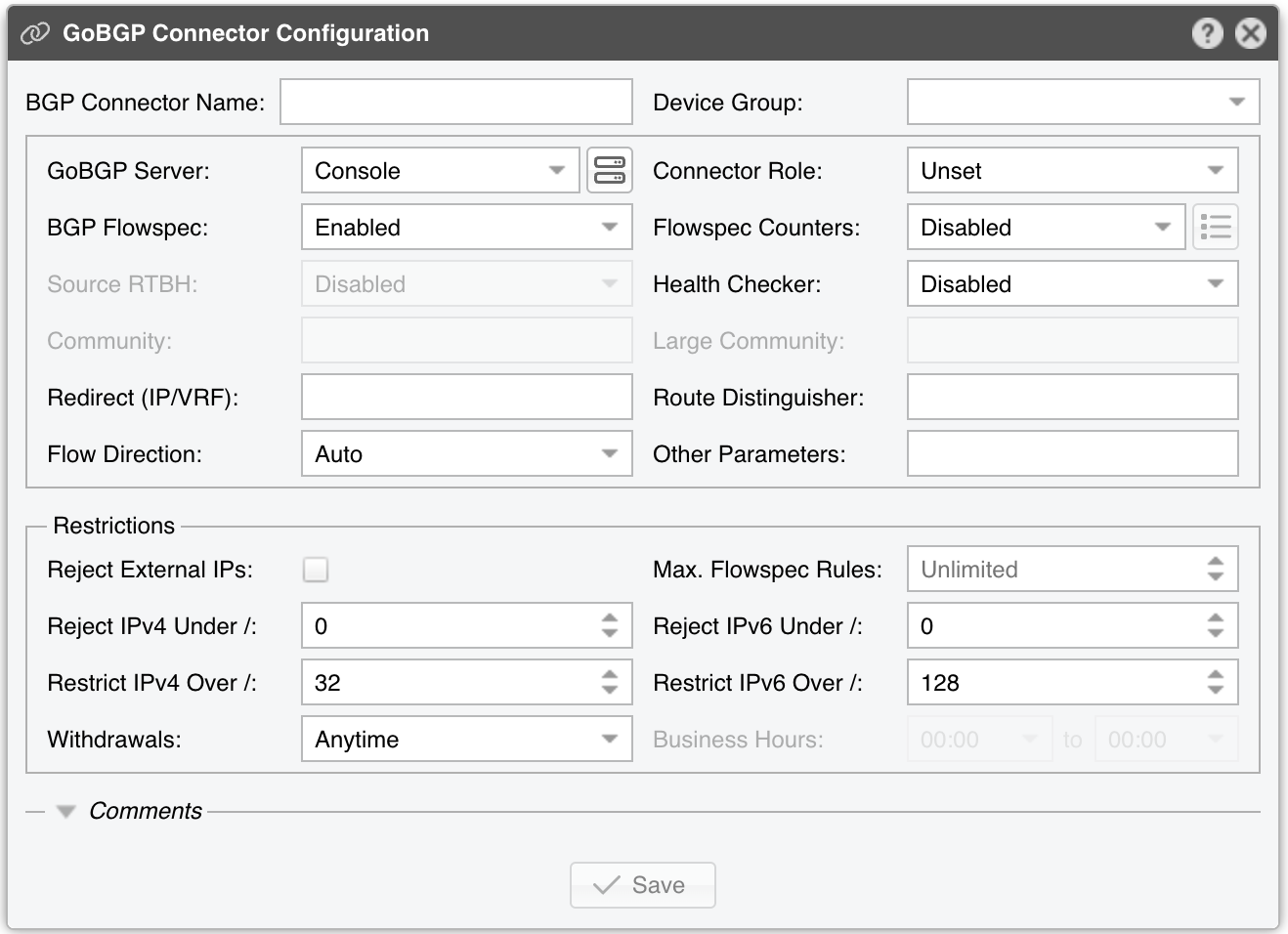
GoBGP Connector Configuration parameters:
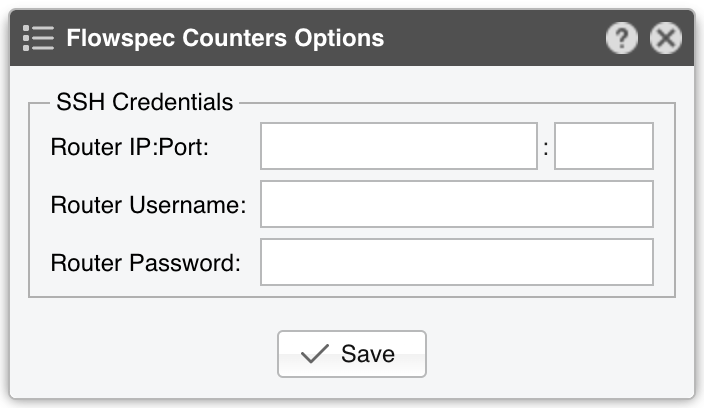
● BGP Connector Name – A short name or description for the GoBGP Connector● Device Group – Enter a description if you wish to organize components (e.g. by location, characteristics) or to permit fine-grained access for roles● GoBGP Server – Select a server that runs GoBGP● Connector Role – Setting the correct role influences the Actions shown in the New Flowspec Rule window and the priority given when there are overlapping announcements by different BGP Connectors with different roles. Prevents mitigation announcements being overwritten by similar diversion announcements▪ Mitigation – Select if the Connector is used for null routing or traffic filtering▪ Diversion – Select if the Connector is used for traffic diversion● BGP Flowspec – Enable if the router supports BGP Flowspec. If the router doesn’t support Flowspec, consider using a Quagga Connector instead● Flowspec Counters – Since there is no vendor-neutral standard for reporting information about the packets and bytes dropped by Flowspec rules, this functionality is limited to only two options:▪ Disabled – The matched counters are not visible in Wanguard▪ Juniper MX – Wanguard connects by SSH to a Juniper MX router using the credentials entered when clicking the options button from the right. Every few seconds, the command “show firewall filter __flowspec_default_inet__” is executed on the router. The output is parsed, and the counters are matched with the known rules● Source RTBH – Enable if the BGP Connector is used for S/RTBH, which should not be confused with the much more popular Destination RTBH. Very few networks support this functionality● Health Checker – When enabled, the status of the BGP peers is checked every minute, and when a BGP peer is down, a warning is written in the event log. You can view the status of the BGP peers in Reports » Devices » Overview● Community – BGP community or list of BGP communities to be appended to each announcement. Not mandatory● Large Community – BGP large community or list of BGP large communities to be appended to each announcement. Not mandatory● Redirect (IP/VRF) – Optional parameter for diversion. Can be an IP, VRF, or “self”● Route Distinguisher – An optional rd value to be passed with each announcement● Flow Direction – Switches the source IP with the destination IP in each announcement. Set to “Inverted” only when doing symmetric routing● Other Parameters – Other parameters that will be passed with each announcement, such as local-preference or as-path, in gobgp’s format, separated by a semicolon● Reject External IPs – When checked, it permits only announcements for the prefixes defined in an IP Zone● Max. Flowspec Rules – The number of Flowspec rules accepted by routers is limited, so you may have to enter your router’s limit here to prevent overflowing the Flowspec table size. Limits published by vendors: Alcatel-Lucent 512, Cisco (ASR9k) 3000, Juniper 8000● Reject IPv4 under / – Restricts sending prefixes that have the IPv4 CIDR mask less than the configured value. For example, a value of 32 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Reject IPv6 under / – Restricts sending prefixes that have the IPv6 CIDR mask less than the configured value. For example, a value of 128 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Restrict IPv4 over / – Set to the maximum IPv4 CIDR mask accepted by your cloud-based DDoS mitigation providers. For example, if your BGP peers accept only /24 prefixes, and you want to announce a whole C class for a single attacked IP, set it to 24. To disable this feature enter the value 32● Restrict IPv6 over / – Set to the maximum IPv6 CIDR mask accepted by your cloud-based DDoS mitigation providers. To disable this feature enter the value 128● Withdrawals – The withdrawal of announcements can be delayed until the time interval specified in the Business Hours field has passed● Comments – Comments about the GoBGP Connector can be saved here. These observations are not visible elsewhere
To enable the GoBGP Connector, click the small on/off switch button displayed next to its name in the Configuration » Components panel.
After the GoBGP Connector is enabled, it can be used by Wanguard Sensor and Wanguard Filter when a Response activates it. To mitigate attacks automatically using Flowspec, configure a Wanguard Filter, and add the “Announce a BGP routing update with Flowspec or S/RTBH” action from the “When a filtering rule is detected” panel of the Response.
Wanguard Console users can send Flowspec announcements via the GoBGP Connector in Reports » Tools » Routing » [Add Flowspec Rule]. Console users can also use the REST API to send Flowspec announcements from any scripting language.
All BGP routing updates are logged in Reports » Tools » Routing » BGP Announcement Archive. If you encounter errors, check the BGP Connector Troubleshooting steps.
20.1.1. GoBGP Installation¶
Wanguard connects to gobgpd using the GoBGP Connector described in the previous section. The configuration of gobgp.conf exceeds the scope of this documentation. In the Network Integration Guideline chapter, you can find some information about various deployment scenarios and the configuration needed on the routers.
The installation process varies according to the Linux distribution and GoBGP version.
Install and enable GoBGP from the repository:
[root@localhost ~]# apt install gobgp
Create the exabgp config file in /etc/gobgpd.conf. Example:
[global.config]
as = 65001
router-id = "192.168.1.1"
[[neighbors]]
[neighbors.config]
neighbor-address = "192.168.1.2"
peer-as = 65001
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv4-flowspec"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv6-flowspec"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv4-unicast"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv6-unicast"
Start and check the gobgp service:
[root@localhost ~]# systemctl enable gobgp
[root@localhost ~]# systemctl start gobgp
[root@localhost ~]# systemctl status gobgp
[root@localhost ~]# gobgp nei
On RHEL, Rocky or AlmaLinux execute:
[root@localhost ~]# yum install gobgp
Create the gobgp config file in /etc/gobgpd.conf. Example:
[global.config]
as = 65001
router-id = "192.168.1.1"
[[neighbors]]
[neighbors.config]
neighbor-address = "192.168.1.2"
peer-as = 65001
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv4-flowspec"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv6-flowspec"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv4-unicast"
[[neighbors.afi-safis]]
[neighbors.afi-safis.config]
afi-safi-name = "ipv6-unicast"
Start and check the gobgp service:
[root@localhost ~]# systemctl enable gobgp
[root@localhost ~]# systemctl start gobgp
[root@localhost ~]# systemctl status gobgp
[root@localhost ~]# gobgp nei
20.2. ExaBGP Connector¶
Before you add an ExaBGP Connector, you must have a previously-configured, fully-functional exabgpd. If you do not, jump to the ExaBGP installation section. You can have a single exabgp and many ExaBGP Connectors using it, which is useful if you need to send announcements with different parameters, e.g., when using multiple communities.
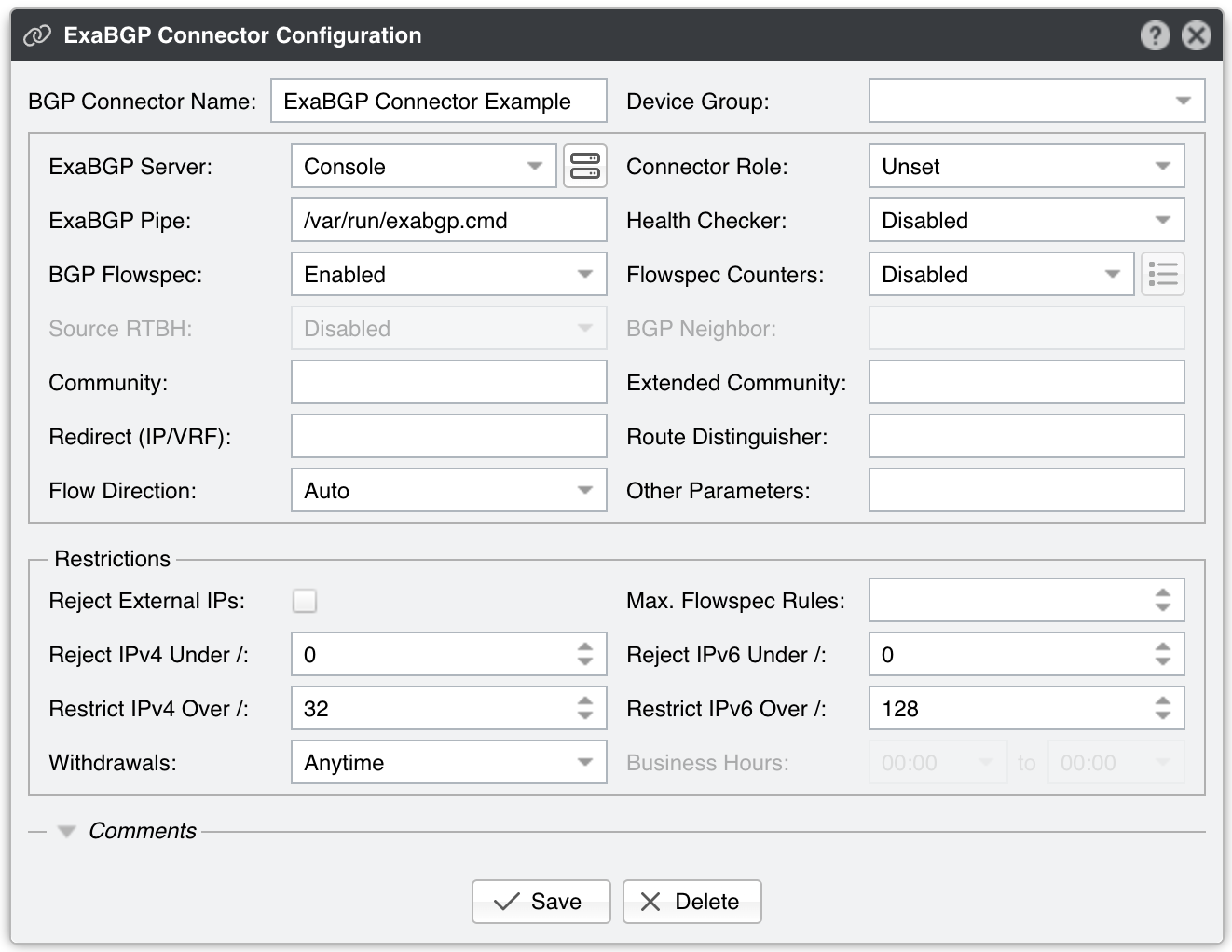
ExaBGP Connector Configuration parameters:
● BGP Connector Name – A short name or description for the ExaBGP Connector● Device Group – Enter a description if you wish to organize components (e.g. by location, characteristics) or to permit fine-grained access for roles● ExaBGP Server – Select a server that runs ExaBGP● Connector Role – Setting the correct role influences the Actions shown in the New Flowspec Rule window and the priority given when there are overlapping announcements by different BGP Connectors with different roles. Prevents mitigation announcements being overwritten by similar diversion announcements▪ Mitigation – Select if the Connector is used for null routing or traffic filtering▪ Diversion – Select if the Connector is used for traffic diversion● ExaBGP Pipe – Mandatory path to the pipe file used to control exabgp. The file must be writeable by the “andrisoft” system account● Health Checker – When enabled, the existence of the ExaBGP Pipe file is checked every minute. If the file doesn’t exist, a warning is written in the event log. The status of the BGP peers is checked too, and when a BGP peer is down, another warning is written in the event log. You can view the status of the BGP peers in Reports » Devices » Overview. This functionality needs a working “exabgpcli show neighbor summary” command, executed by the “andrisoft” user● BGP Flowspec – Enable if the router supports BGP Flowspec. If the router doesn’t support Flowspec, consider using a Quagga Connector instead● Flowspec Counters – Since there is no vendor-neutral standard for reporting information about the packets and bytes dropped by Flowspec rules, this functionality is limited to only two options:▪ Disabled – The matched counters are not visible in Wanguard▪ Juniper MX – Wanguard connects by SSH to a Juniper MX router using the credentials entered when clicking the options button from the right. Every few seconds, the command “show firewall filter __flowspec_default_inet__” is executed on the router. The output is parsed, and the counters are matched with the known rules● Source RTBH – Enable if the BGP Connector is used for S/RTBH, which should not be confused with the much more popular Destination RTBH. Very few networks support this functionality● BGP Neighbor – Optional parameter used to distinguish between multiple BGP neighbors● Community – BGP community or list of BGP communities to be appended to each announcement. Not mandatory● Extended Community – BGP extended community or list of BGP extended communities to be appended to each announcement. Not mandatory● Redirect (IP/VRF) – Optional parameter for diversion. Can be an IP, VRF, or “self”● Route Distinguisher – An optional rd value to be passed with each announcement● Flow Direction – Switches the source IP with the destination IP in each announcement. Set to “Inverted” only when doing symmetric routing● Other Parameters – Other parameters that will be passed with each announcement, such as local-preference or as-path, in exabgp.conf’s format, separated by a semicolon● Reject External IPs – When checked, it permits only announcements for the prefixes defined in an IP Zone● Max. Flowspec Rules – The number of Flowspec rules accepted by routers is limited, so you may have to enter your router’s limit here to prevent overflowing the Flowspec table size. Limits published by vendors: Alcatel-Lucent 512, Cisco (ASR9k) 3000, Juniper 8000● Reject IPv4 under / – Restricts sending prefixes that have the IPv4 CIDR mask less than the configured value. For example, a value of 32 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Reject IPv6 under / – Restricts sending prefixes that have the IPv6 CIDR mask less than the configured value. For example, a value of 128 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Restrict IPv4 over / – Set to the maximum IPv4 CIDR mask accepted by your cloud-based DDoS mitigation providers. For example, if your BGP peers accept only /24 prefixes, and you want to announce a whole C class for a single attacked IP, set it to 24. To disable this feature enter the value 32● Restrict IPv6 over / – Set to the maximum IPv6 CIDR mask accepted by your cloud-based DDoS mitigation providers. To disable this feature enter the value 128● Withdrawals – The withdrawal of announcements can be delayed until the time interval specified in the Business Hours field has passed● Comments – Comments about the ExaBGP Connector can be saved here. These observations are not visible elsewhere
To enable the ExaBGP Connector, click the small on/off switch button displayed next to its name in the Configuration » Components panel.
After the ExaBGP Connector is enabled, it can be used by Wanguard Sensor and Wanguard Filter when a Response activates it. To mitigate attacks automatically using Flowspec, configure a Wanguard Filter, and add the “Announce a BGP routing update with Flowspec or S/RTBH” action from the “When a filtering rule is detected” panel of the Response.
Wanguard Console users can send Flowspec announcements via the ExaBGP Connector in Reports » Tools » Routing » [Add Flowspec Rule]. Console users can also use the REST API to send Flowspec announcements from any scripting language.
All BGP routing updates are logged in Reports » Tools » Routing » BGP Announcement Archive. If you encounter errors, check the BGP Connector Troubleshooting steps.
20.2.1. ExaBGP Installation¶
Wanguard connects to exabgpd using the ExaBGP Connector described in the previous section. The configuration of exabgp.conf exceeds the scope of this documentation. In the Network Integration Guideline chapter, you can find some information about various deployment scenarios and the configuration needed on the routers.
The installation process varies according to the Linux distribution and ExaBGP version.
Install and enable ExaBGP from the package repository:
[root@localhost ~]# apt install exabgp
[root@localhost ~]# systemctl enable exabgp
Create the exabgp config file in /etc/exabgp/exabgp.conf. Example:
neighbor 10.0.0.2 {
router-id 10.0.0.1;
local-address 10.0.0.1;
local-as 65000;
peer-as 65000;
}
Start and check the exabgp service:
[root@localhost ~]# systemctl start exabgp
[root@localhost ~]# systemctl status exabgp
Enter /run/exabgp/exabgp.in in the ExaBGP Pipe field from the ExaBGP Connector.
Download and extract ExaBGP 4.2 from github to /opt/exabgp:
[root@localhost ~]# wget https://github.com/Exa-Networks/exabgp/archive/refs/heads/4.2.zip
[root@localhost ~]# mv 4.2.zip /opt
[root@localhost ~]# cd /opt
[root@localhost opt]# unzip 4.2.zip
[root@localhost opt]# mv exabgp-4.2 exabgp
On RHEL 8, Rocky 8 or AlmaLinux 8 execute:
[root@localhost ~]# yum install python39
Create the file /lib/systemd/system/exabgp.service and add the content:
[Unit]
Description=ExaBGP
Documentation=man:exabgp(1)
Documentation=man:exabgp.conf(5)
Documentation=https://github.com/Exa-Networks/exabgp/wiki
After=network.target
ConditionPathExists=/etc/exabgp/exabgp.conf
[Service]
Environment=exabgp_daemon_daemonize=false
ExecStartPre=/bin/bash -c "/usr/bin/mkfifo -m 0666 /run/exabgp/exabgp.{in,out}"
ExecStopPost=/bin/bash -c "/bin/rm -f /run/exabgp/exabgp.{in,out}"
ExecStart=/opt/exabgp/sbin/exabgp /etc/exabgp/exabgp.conf
ExecReload=/bin/kill -USR1 $MAINPID
[Install]
WantedBy=multi-user.target
Create the exabgp config file in /etc/exabgp/exabgp.conf. Example:
neighbor 10.0.0.2 {
router-id 10.0.0.1;
local-address 10.0.0.1;
local-as 65000;
peer-as 65000;
}
Start and check the exabgp service:
[root@localhost ~]# systemctl daemon-reload
[root@localhost ~]# systemctl enable exabgp
[root@localhost ~]# systemctl start exabgp
[root@localhost ~]# systemctl status exabgp
Enter /run/exabgp/exabgp.in in the ExaBGP Pipe field from the ExaBGP Connector.
Install ExaBGP from the package repository:
[root@localhost ~]# apt install exabgp
Create the exabgp config file in /etc/exabgp/exabgp.conf. Example:
neighbor 10.0.0.2 {
router-id 10.0.0.1;
local-address 10.0.0.1;
local-as 65000;
peer-as 65000;
}
Edit the file /lib/systemd/system/exabgp.service:
Enable:
User=exabgp
Group=exabgp
Add:
ExecStopPost=/bin/bash -c "/bin/rm -f /run/exabgp/exabgp.{in,out}"
Replace:
ExecStartPre=chmod 600 /run/exabgp/exabgp.in
ExecStartPre=chmod 600 /run/exabgp/exabgp.out
With:
ExecStartPre=chmod 777 /run/exabgp/exabgp.in
ExecStartPre=chmod 777 /run/exabgp/exabgp.out
Start and check the exabgp service:
[root@localhost ~]# systemctl daemon-reload
[root@localhost ~]# systemctl enable exabgp
[root@localhost ~]# systemctl start exabgp
[root@localhost ~]# systemctl status exabgp
Enter /run/exabgp/exabgp.in in the ExaBGP Pipe field from the ExaBGP Connector.
On Debian / Ubuntu systems, install ExaBGP 4.0 from git, then install the wanbgp and socat packages by executing:
[root@localhost ~]# apt-get install wanbgp socat
On Red Hat / CentOS systems, install ExaBGP 4.0 from git, then install the wanbgp and socat packages by executing:
[root@localhost ~]# yum install wanbgp socat
The “process” and “api” sections from the configuration file listed below are mandatory. The rest of the lines are given as an example.
process announce-routes {
run /usr/bin/socat stdout pipe:/var/run/exabgp.cmd;
encoder json;
}
neighbor 192.168.50.1 {
# ID for this ExaBGP router
router-id 192.168.50.2;
local-address 192.168.50.2;
# local AS number
local-as 65001;
# remote AS number
peer-as 12345;
group-updates false;
family {
ipv4 flow;
}
api {
processes [ announce-routes ];
}
}
Start ExaBGP 4.0 with a command such as:
env exabgp.daemon.user=root exabgp.daemon.daemonize=true exabgp.daemon.pid=/var/run/exabgp.pid exabgp.log.destination=/var/log/exabgp.log /opt/exabgp4/sbin/exabgp /etc/exabgp_example.conf
Verify that ExaBGP 4.0 starts and functions correctly by inspecting /var/log/exabgp.log.
20.3. Quagga Connector¶
Before you add a Quagga Connector, you must have a previously-configured, fully-functional bgpd. If you do not, jump to the Quagga / FRR installation section. You can have a single bgpd and many Quagga Connectors using it, which is helpful if you need to send announcements with different parameters, e.g., when using multiple route-maps to send different communities.
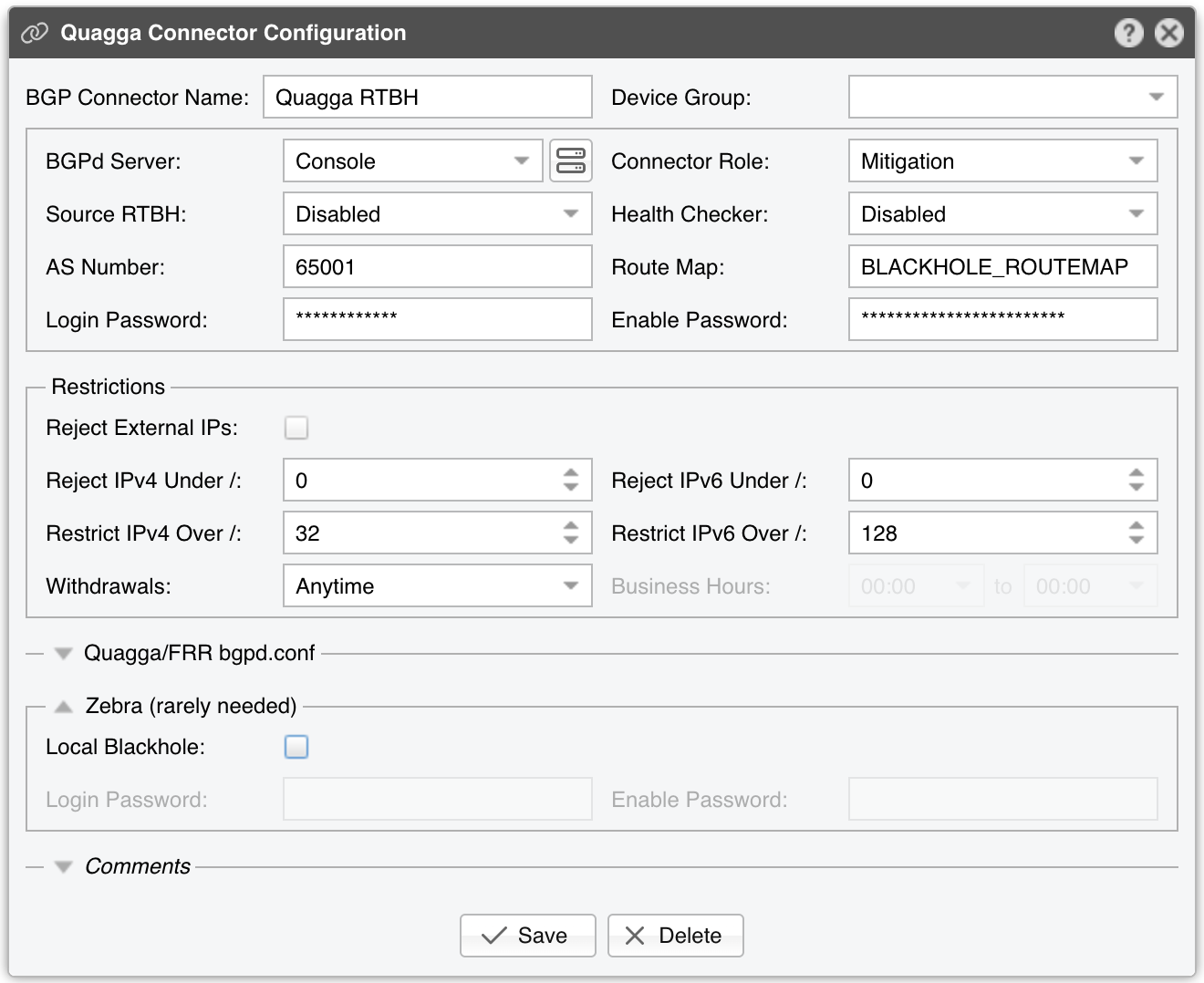
Quagga Connector Configuration parameters:
● BGP Connector Name – A short name or description of the Quagga Connector● Device Group – Enter a description if you wish to organize components (e.g. by location, characteristics) or to permit fine-grained access for roles● Connector Role – Setting the correct role influences the Actions shown in Reports » Tools » Routing and the priority given when there are overlapping announcements by different BGP Connectors with different roles. Prevents mitigation announcements being overwritten by similar diversion announcements▪ Mitigation – Select if the Connector is used for null routing or traffic filtering▪ Diversion – Select if the Connector is used for traffic diversion● Source RTBH – Enable if the BGP Connector is used for S/RTBH, which should not be confused with the much more popular Destination RTBH. Very few networks support this functionality● Health Checker – When enabled, the status of the BGP peers is checked every minute. When a BGP peer is down, a warning is written in the event log. You can view the status of the BGP peers in Reports » Devices » Overview● AS Number – Enter the same AS number used in the bgpd configuration● Route Map – A route-map that will be used for each announcement. This option is not mandatory but widely used to append communities to the routing update. If you need to use multiple route maps, define multiple Quagga Connectors, one for each route map● AS View – If multiple AS views are defined in the bgpd configuration, enter the AS view you want to use for this Quagga Connector. This option is not mandatory and is rarely used● Login Password – Password needed to connect to the bgpd daemon● Enable Password – Configuration mode password of the bgpd daemon● Reject External IPs – When checked, it permits only announcements for the prefixes defined in an IP Zone● Reject IPv4 under / – Restricts sending prefixes that have the IPv4 CIDR mask less than the configured value. For example, a value of 32 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Reject IPv6 under / – Restricts sending prefixes that have the IPv6 CIDR mask less than the configured value. For example, a value of 128 rejects all prefixes that are not hosts and prevents manual or automatic announcements of subnets. To disable this feature enter the value 0● Restrict IPv4 over / – Set to the maximum IPv4 CIDR mask accepted by your cloud-based DDoS mitigation providers. For example, if your BGP peers accept only /24 prefixes, and you want to announce a whole C class for a single attacked IP, set it to 24. To disable this feature enter the value 32● Restrict IPv6 over / – Set to the maximum IPv6 CIDR mask accepted by your cloud-based DDoS mitigation providers. To disable this feature enter the value 128● Quagga/FRR bgpd.conf – The content of the bgpd.conf file can be viewed and changed from the CLI or the user interface. The file’s location is determined by the Linux Distribution parameter from Configuration » Servers. If you replaced the default daemon that came with the distribution, edit the file and restart bgpd only from CLI. The bgpd.conf file uses a format very similar to the Cisco IOS configuration format. Quagga’s documentation covers the configuration options● Zebra Local Black Hole – Check if you need the local black hole feature provided by the Zebra daemon. This rarely-used feature is useful only for inline servers● Zebra Login & Enable Password – Credentials required to connect to the zebra daemon● Comments – Comments about the Quagga Connector can be saved here. These observations are not visible elsewhere
To enable the Quagga Connector, click the small on/off switch button displayed next to its name in the Configuration » Components panel.
After the Quagga Connector is enabled, it can be used by Wanguard Sensor when a Response activates it.
Wanguard Console users can send black hole or diversion announcements via the Quagga Connector in Reports » Tools » Routing » [Create Blackhole] or [Divert Traffic]. Console users can also use the REST API to send BGP announcements from any scripting language.
20.3.1. Quagga / FRR Installation¶
Wanguard sends and withdraws BGP announcements via the bgpd daemon provided by Quagga or FRR. The installation instructions are distribution-specific:
Install FRR, then edit /etc/frr/daemons. Change bgpd=no to bgpd=yes and remove the string “-A 127.0.0.1” from the bgpd_options line.
[root@localhost ~]# apt install frr
[root@localhost ~]# nano /etc/frr/daemons
To be able to start the bgpd service, create a basic configuration file. Setting a password for the bgpd daemon is usually enough to get it started. Replace “bgppass” with your own password.
[root@localhost ~]# echo 'password bgppass' > /etc/frr/bgpd.conf
[root@localhost ~]# echo 'enable password bgppass' >> /etc/frr/bgpd.conf
[root@localhost ~]# chown frr /etc/frr/bgpd.conf
[root@localhost ~]# mv /etc/frr/frr.conf /etc/frr/frr.conf_bak
[root@localhost ~]# systemctl enable frr
[root@localhost ~]# systemctl restart frr
Connect to the bgp daemon with telnet on localhost port 2605 (default bgpd port) and enter the previously-defined password (“bgppass”) when requested.
[root@localhost ~]# telnet 127.0.0.1 2605
localhost> enable
localhost# config terminal
localhost(config)#
Configure bgpd using the commands shown in the following example after adapting them to your own network. Please note that you can use the prefix-list, route-map, or distribute-list method for filtering outgoing routing information. To have a uniform approach, the following example uses route-maps. Optionally, BGP authentication can be configured to increase security and avoid any illegal BGP announcement which may lead to a security breach.
localhost(config)# router bgp <Wanguard-Filter-AS-number>
localhost(config-router)# bgp router-id <Wanguard-Filter-IP-address>
localhost(config-router)# neighbor <Router-IP-address> remote-as <Router-AS-number>
localhost(config-router)# neighbor <Router-IP-address> description <description>
localhost(config-router)# neighbor <Router-IP-address> password <BGP MD5 password>
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-in in
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-out out
localhost(config-router)# no bgp network import-check
localhost(config-router)# exit
localhost(config)# route-map Wanguard-Filter-in deny 10
localhost(config-route-map)# exit
localhost(config)# route-map Wanguard-Filter-out permit 10
localhost(config-route-map)# set community no-advertise <Wanguard-Filter-community>
localhost(config-route-map)# exit
localhost(config)# write
localhost(config)# exit
To display the bgpd configuration, enter the show running-config command from the “enable” command level. In the following example, the router’s AS number is 1000, and the BGPd AS number is 65000.
The following partial sample output is displayed:
localhost# show running-config
... skipped ...
router bgp 65000
bgp router-id 192.168.1.100
no bgp network import-check
neighbor 192.168.1.1 remote-as 1000
neighbor 192.168.1.1 description divert-from router
neighbor 192.168.1.1 soft-reconfiguration inbound
neighbor 192.168.1.1 route-map Wanguard-Filter-in in
neighbor 192.168.1.1 route-map Wanguard-Filter-out out
!
route-map Wanguard-Filter-in deny 10
!
route-map Wanguard-Filter-out permit 10
set community no-advertise
!
line vty
... skipped ...
Install FRR, then edit /etc/frr/daemons. Change bgpd=no to bgpd=yes and remove the string “-A 127.0.0.1” from the bgpd_options line.
[root@localhost ~]# apt install frr
[root@localhost ~]# nano /etc/frr/daemons
To be able to start the bgpd service, create a basic configuration file. Setting a password for the bgpd daemon is usually enough to get it started. Replace “bgppass” with your own password.
[root@localhost ~]# echo 'password bgppass' > /etc/frr/bgpd.conf
[root@localhost ~]# echo 'enable password bgppass' >> /etc/frr/bgpd.conf
[root@localhost ~]# chown frr /etc/frr/bgpd.conf
[root@localhost ~]# ln -s /etc/frr/bgpd.conf /etc/frr/frr.conf
[root@localhost ~]# systemctl enable frr
[root@localhost ~]# systemctl restart frr
Connect to the bgp daemon with telnet on localhost port 2605 (default bgpd port) and enter the previously-defined password (“bgppass”) when requested.
[root@localhost ~]# telnet 127.0.0.1 2605
localhost> enable
localhost# config terminal
localhost(config)#
Configure bgpd using the commands shown in the following example after adapting them to your own network. Please note that you can use the prefix-list, route-map, or distribute-list method for filtering outgoing routing information. To have a uniform approach, the following example uses route-maps. Optionally, BGP authentication can be configured to increase security and avoid any illegal BGP announcement which may lead to a security breach.
localhost(config)# router bgp <Wanguard-Filter-AS-number>
localhost(config-router)# bgp router-id <Wanguard-Filter-IP-address>
localhost(config-router)# neighbor <Router-IP-address> remote-as <Router-AS-number>
localhost(config-router)# neighbor <Router-IP-address> description <description>
localhost(config-router)# neighbor <Router-IP-address> password <BGP MD5 password>
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-in in
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-out out
localhost(config-router)# no bgp network import-check
localhost(config-router)# exit
localhost(config)# route-map Wanguard-Filter-in deny 10
localhost(config-route-map)# exit
localhost(config)# route-map Wanguard-Filter-out permit 10
localhost(config-route-map)# set community no-advertise <Wanguard-Filter-community>
localhost(config-route-map)# exit
localhost(config)# write
localhost(config)# exit
To display the bgpd configuration, enter the show running-config command from the “enable” command level. In the following example, the router’s AS number is 1000, and the BGPd AS number is 65000.
The following partial sample output is displayed:
localhost# show running-config
... skipped ...
router bgp 65000
bgp router-id 192.168.1.100
no bgp network import-check
neighbor 192.168.1.1 remote-as 1000
neighbor 192.168.1.1 description divert-from router
neighbor 192.168.1.1 soft-reconfiguration inbound
neighbor 192.168.1.1 route-map Wanguard-Filter-in in
neighbor 192.168.1.1 route-map Wanguard-Filter-out out
!
route-map Wanguard-Filter-in deny 10
!
route-map Wanguard-Filter-out permit 10
set community no-advertise
!
line vty
... skipped ...
Install Quagga, then remove the loopback binding (” -A 127.0.0.1”) from the /lib/systemd/system/bgpd.service file.
[root@localhost ~]# apt install quagga
[root@localhost ~]# nano /lib/systemd/system/bgpd.service
[root@localhost ~]# systemctl daemon-reload
To be able to start the bgpd service, create a basic configuration file. Setting a password for the bgpd daemon is usually enough to get it started. Replace “bgppass” with your own password. On these systems, bgpd starts only when zebra is running.
[root@localhost ~]# echo 'password bgppass' > /etc/quagga/bgpd.conf
[root@localhost ~]# echo 'enable password bgppass' >> /etc/quagga/bgpd.conf
[root@localhost ~]# chown quagga /etc/quagga/bgpd.conf
[root@localhost ~]# touch /etc/quagga/zebra.conf
[root@localhost ~]# systemctl start zebra
[root@localhost ~]# systemctl enable zebra
[root@localhost ~]# systemctl start bgpd
[root@localhost ~]# systemctl enable bgpd
Connect to the bgp daemon with telnet on localhost port 2605 (default bgpd port) and enter the previously-defined password (“bgppass”) when requested.
[root@localhost ~]# telnet 127.0.0.1 2605
localhost> enable
localhost# config terminal
localhost(config)#
Configure bgpd using the commands shown in the following example after adapting them to your own network. Please note that you can use the prefix-list, route-map, or distribute-list method for filtering outgoing routing information. To have a uniform approach, the following example uses route-maps. Optionally, BGP authentication can be configured to increase security and avoid any illegal BGP announcement which may lead to a security breach.
localhost(config)# router bgp <Wanguard-Filter-AS-number>
localhost(config-router)# bgp router-id <Wanguard-Filter-IP-address>
localhost(config-router)# neighbor <Router-IP-address> remote-as <Router-AS-number>
localhost(config-router)# neighbor <Router-IP-address> description <description>
localhost(config-router)# neighbor <Router-IP-address> password <BGP MD5 password>
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-in in
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-out out
localhost(config-router)# exit
localhost(config)# route-map Wanguard-Filter-in deny 10
localhost(config-route-map)# exit
localhost(config)# route-map Wanguard-Filter-out permit 10
localhost(config-route-map)# set community no-advertise <Wanguard-Filter-community>
localhost(config-route-map)# exit
localhost(config)# write
localhost(config)# exit
To display the bgpd configuration, enter the show running-config command from the “enable” command level. In the following example, the router’s AS number is 1000, and the BGPd AS number is 65000.
The following partial sample output is displayed:
localhost# show running-config
... skipped ...
router bgp 65000
bgp router-id 192.168.1.100
neighbor 192.168.1.1 remote-as 1000
neighbor 192.168.1.1 description divert-from router
neighbor 192.168.1.1 soft-reconfiguration inbound
neighbor 192.168.1.1 route-map Wanguard-Filter-in in
neighbor 192.168.1.1 route-map Wanguard-Filter-out out
!
route-map Wanguard-Filter-in deny 10
!
route-map Wanguard-Filter-out permit 10
set community no-advertise
!
line vty
... skipped ...
Install FRR, then edit /etc/frr/daemons. Change bgpd=no to bgpd=yes and remove the string “-A 127.0.0.1” from the bgpd_options line.
[root@localhost ~]# yum install frr
[root@localhost ~]# nano /etc/frr/daemons
To be able to start the bgpd service, create a basic configuration file. Setting a password for the bgpd daemon is usually enough to get it started. Replace “bgppass” with your own password.
[root@localhost ~]# echo 'password bgppass' > /etc/frr/bgpd.conf
[root@localhost ~]# echo 'enable password bgppass' >> /etc/frr/bgpd.conf
[root@localhost ~]# chown frr /etc/frr/bgpd.conf
[root@localhost ~]# systemctl enable frr
[root@localhost ~]# systemctl start frr
Connect to the bgp daemon with telnet on localhost port 2605 (default bgpd port) and enter the previously-defined password (“bgppass”) when requested.
[root@localhost ~]# telnet 127.0.0.1 2605
localhost> enable
localhost# config terminal
localhost(config)#
Configure bgpd using the commands shown in the following example after adapting them to your own network. Please note that you can use the prefix-list, route-map, or distribute-list method for filtering outgoing routing information. To have a uniform approach, the following example uses route-maps. Optionally, BGP authentication can be configured to increase security and avoid any illegal BGP announcement which may lead to a security breach.
localhost(config)# router bgp <Wanguard-Filter-AS-number>
localhost(config-router)# bgp router-id <Wanguard-Filter-IP-address>
localhost(config-router)# neighbor <Router-IP-address> remote-as <Router-AS-number>
localhost(config-router)# neighbor <Router-IP-address> description <description>
localhost(config-router)# neighbor <Router-IP-address> password <BGP MD5 password>
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-in in
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-out out
localhost(config-router)# exit
localhost(config)# route-map Wanguard-Filter-in deny 10
localhost(config-route-map)# exit
localhost(config)# route-map Wanguard-Filter-out permit 10
localhost(config-route-map)# set community no-advertise <Wanguard-Filter-community>
localhost(config-route-map)# exit
localhost(config)# write
localhost(config)# exit
To display the bgpd configuration, enter the show running-config command from the “enable” command level. In the following example, the router’s AS number is 1000, and the BGPd AS number is 65000.
The following partial sample output is displayed:
localhost# show running-config
... skipped ...
router bgp 65000
bgp router-id 192.168.1.100
neighbor 192.168.1.1 remote-as 1000
neighbor 192.168.1.1 description divert-from router
neighbor 192.168.1.1 soft-reconfiguration inbound
neighbor 192.168.1.1 route-map Wanguard-Filter-in in
neighbor 192.168.1.1 route-map Wanguard-Filter-out out
!
route-map Wanguard-Filter-in deny 10
!
route-map Wanguard-Filter-out permit 10
set community no-advertise
!
line vty
... skipped ...
Install Quagga, then edit /etc/sysconfig/quagga and replace BGPD_OPTS=”-A 127.0.0.1” with BGPD_OPTS=””.
[root@localhost ~]# yum install quagga
[root@localhost ~]# nano /etc/sysconfig/quagga
To be able to start the bgpd service, create a basic configuration file. Setting a password for the bgpd daemon is usually enough to get it started. Replace “bgppass” with your own password.
[root@localhost ~]# echo 'password bgppass' > /etc/quagga/bgpd.conf
[root@localhost ~]# echo 'enable password bgppass' >> /etc/quagga/bgpd.conf
[root@localhost ~]# chown quagga /etc/quagga/bgpd.conf
[root@localhost ~]# systemctl start bgpd
[root@localhost ~]# systemctl enable bgpd
Connect to the bgp daemon with telnet on localhost port 2605 (default bgpd port) and enter the previously-defined password (“bgppass”) when requested.
[root@localhost ~]# telnet 127.0.0.1 2605
localhost> enable
localhost# config terminal
localhost(config)#
Configure bgpd using the commands shown in the following example after adapting them to your own network. Please note that you can use the prefix-list, route-map, or distribute-list method for filtering outgoing routing information. To have a uniform approach, the following example uses route-maps. Optionally, BGP authentication can be configured to increase security and avoid any illegal BGP announcement which may lead to a security breach.
localhost(config)# router bgp <Wanguard-Filter-AS-number>
localhost(config-router)# bgp router-id <Wanguard-Filter-IP-address>
localhost(config-router)# neighbor <Router-IP-address> remote-as <Router-AS-number>
localhost(config-router)# neighbor <Router-IP-address> description <description>
localhost(config-router)# neighbor <Router-IP-address> password <BGP MD5 password>
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-in in
localhost(config-router)# neighbor <Router-IP-address> route-map Wanguard-Filter-out out
localhost(config-router)# exit
localhost(config)# route-map Wanguard-Filter-in deny 10
localhost(config-route-map)# exit
localhost(config)# route-map Wanguard-Filter-out permit 10
localhost(config-route-map)# set community no-advertise <Wanguard-Filter-community>
localhost(config-route-map)# exit
localhost(config)# write
localhost(config)# exit
To display the bgpd configuration, enter the show running-config command from the “enable” command level. In the following example, the router’s AS number is 1000, and the BGPd AS number is 65000.
The following partial sample output is displayed:
localhost# show running-config
... skipped ...
router bgp 65000
bgp router-id 192.168.1.100
neighbor 192.168.1.1 remote-as 1000
neighbor 192.168.1.1 description divert-from router
neighbor 192.168.1.1 soft-reconfiguration inbound
neighbor 192.168.1.1 route-map Wanguard-Filter-in in
neighbor 192.168.1.1 route-map Wanguard-Filter-out out
!
route-map Wanguard-Filter-in deny 10
!
route-map Wanguard-Filter-out permit 10
set community no-advertise
!
line vty
... skipped ...
20.3.2. IPv4 and IPv6 in Quagga / FRR¶
The bgpd.conf excerpt below illustrates an example of IPv4 and IPv6 RTBH (Remotely Triggered Black Hole). Two communities were used. Community 667 is for the own infrastructure to avoid on RTBH our self. It is not installed on the RIB and only sent to upstreams.
router bgp 65002
bgp router-id 198.51.100.220
no bgp default ipv4-unicast
neighbor 198.51.100.77 remote-as 65000
neighbor 198.51.100.77 description RouteReflector1
neighbor 198.51.100.77 ebgp-multihop 10
neighbor 198.51.100.77 activate
neighbor 198.51.100.77 route-map RM-DENY in
neighbor 198.51.100.77 route-map RM-IPV4-ADVERTISE-NULL out
neighbor 198.51.100.88 remote-as 65000
neighbor 198.51.100.88 description RouteReflector2
neighbor 198.51.100.88 ebgp-multihop 10
neighbor 198.51.100.88 activate
neighbor 198.51.100.88 route-map RM-DENY in
neighbor 198.51.100.88 route-map RM-IPV4-ADVERTISE-NULL out
neighbor 2001:DB8::77 remote-as 65000
neighbor 2001:DB8::77 description RouteReflector1
neighbor 2001:DB8::77 ebgp-multihop 10
neighbor 2001:DB8::77 override-capability
neighbor 2001:DB8::88 remote-as 65000
neighbor 2001:DB8::88 description RouteReflector2
neighbor 2001:DB8::88 ebgp-multihop 10
!
address-family ipv6
neighbor 2001:DB8::77 activate
neighbor 2001:DB8::77 soft-reconfiguration inbound
neighbor 2001:DB8::77 route-map RM-DENY in
neighbor 2001:DB8::77 route-map RM-IPV6-ADVERTISE-NULL out
neighbor 2001:DB8::88 activate
neighbor 2001:DB8::88 soft-reconfiguration inbound
neighbor 2001:DB8::88 route-map RM-DENY in
neighbor 2001:DB8::88 route-map RM-IPV6-ADVERTISE-NULL out
exit-address-family
!
ip prefix-list PL-IPV4-ANY-AUTOMATIC-RTBH seq 5 permit 0.0.0.0/0 ge 32
ip prefix-list PL-IPV4-INFRA-AUTOMATIC-RTBH seq 5 permit 198.51.100.0/24 le 32
!
ipv6 prefix-list PL-IPV6-ANY-AUTOMATIC-RTBH seq 5 permit ::/0 ge 128
ipv6 prefix-list PL-IPV6-INFRA-AUTOMATIC-RTBH seq 5 permit 2001:DB8::/64 le 128
!
route-map RM-DENY deny 10
!
route-map RM-IPV4-ADVERTISE-NULL permit 10
match ip address prefix-list PL-IPV4-INFRA-AUTOMATIC-RTBH
set community 65000:667
set ip next-hop 198.51.100.220
!
route-map RM-IPV4-ADVERTISE-NULL permit 20
match ip address prefix-list PL-IPV4-ANY-AUTOMATIC-RTBH
set community 65000:666
set ip next-hop 198.51.100.220
!
route-map RM-IPV6-ADVERTISE-NULL permit 10
match ipv6 address prefix-list PL-IPV6-INFRA-AUTOMATIC-RTBH
set community 65000:667
set ipv6 next-hop global 2001:DB8::220
!
route-map RM-IPV6-ADVERTISE-NULL permit 20
match ipv6 address prefix-list PL-IPV6-ANY-AUTOMATIC-RTBH
set community 65000:666
set ipv6 next-hop global 2001:DB8::220
!
Debug commands (2001:DB8::666 and 198.51.100.66 are null routed):
quagga# show vers
Quagga 0.99.24.1 ().
quagga# sh ipv6 bgp summary
BGP router identifier 198.51.100.220, local AS number 65002
RIB entries 1, using 112 bytes of memory
Peers 4, using 18 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2001:DB8::77 4 65000 18675 18683 0 0 0 01:08:19 0
2001:DB8::88 4 65000 18675 18691 0 0 0 00:23:48 0
Total number of neighbors 2
quagga# sh ipv6 bgp neighbors 2001:DB8::88 advertised-routes
Network Next Hop Metric LocPrf Weight Path
*> 2001:DB8::666/128
2001:DB8::220
0 32768 i
quagga# sh ip bgp summary
BGP router identifier 198.51.100.220, local AS number 65002
RIB entries 3, using 336 bytes of memory
Peers 4, using 18 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
198.51.100.77 4 65000 18672 18681 0 0 0 01w5d23h 0
198.51.100.88 4 65000 18671 18681 0 0 0 01w5d23h 0
quagga# sh ip bgp nei 198.51.100.88 advertised-routes
Network Next Hop Metric LocPrf Weight Path
*> 198.51.100.66/32
198.51.100.220 0 32768 i