8. Configuration » General Settings » Custom Decoders¶
Decoders represent internal functions (traffic dissectors) that differentiate and classify the underlying protocols of each packet or flow. The predefined decoders are listed in the “Graphs & Storage” chapter. If you do not need to define custom decoders, you can safely skip this section.
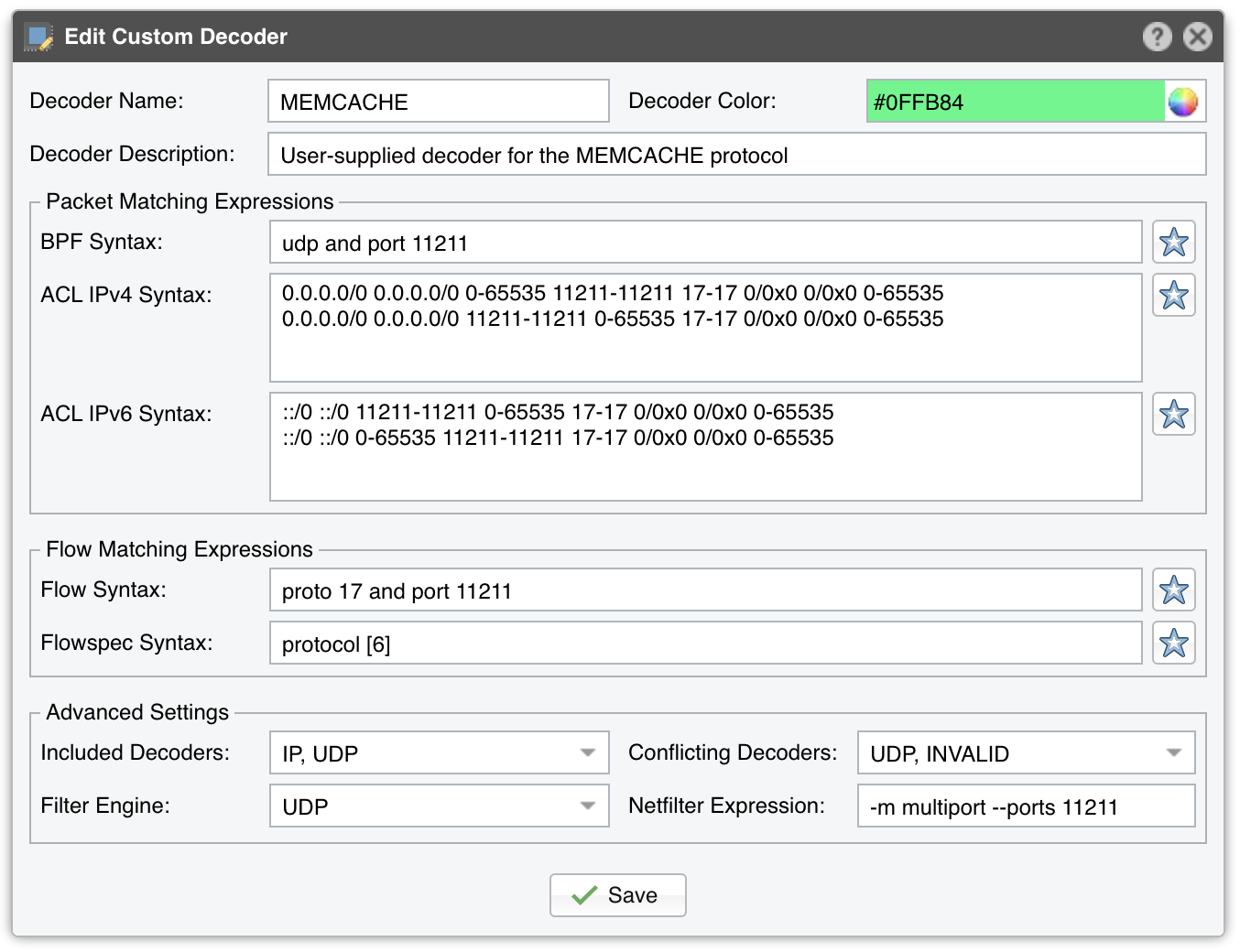
To manage user-defined decoders go to Configuration » General Settings » Custom Decoders. Each custom decoder is defined by:
● Decoder Name – A short name to help you identify the decoder. This field is mandatory
● Decoder Color – The color used in graphs for the decoder. The default color is a random one, which can be changed by entering a different HTML color code or by clicking the drop-down menu
● Decoder Description – An optional short description of the decoder
● BFP Syntax – This syntax is used by Packet Sensor and Packet Filter when the Capture Engine option is not set to DPDK. Click the star icon on the right to see details about the correct syntax. Examples:
◦ To match TCP packets with the SYN flag set, enter tcp[tcpflags] & tcp-syn!=0
◦ To match UDP packets with the destination port under 1024, enter proto 17 and dst portrange 1-1023
◦ To match memcached packets, enter proto 17 and port 11211
● ACL IPv4/IPv6 Syntax – This syntax is used by Packet Sensor and Packet Filter when the Capture Engine option is set to DPDK. Click the star icon on the right to see a few examples and get all the details about the correct syntax
● Flow Syntax – This syntax is used by Flow Sensor and Flow Filter. Click the star icon on the right to see the correct syntax. Examples:
◦ To match TCP flows having only the SYN flag set, enter flags S and not flags AFRPU
◦ To match flows with the MPLS label0 set to 2, enter mpls label0=2
◦ To match memcached packets, enter proto 17 and port 11211
● Flowspec Syntax – Enter a Flowspec expression if you intend to use BGP Flowspec for traffic redirection or DDoS mitigation. Click the star icon on the right to open a window that shows you the correct syntax. Example:
◦ To match memcached packets, enter port 11211; protocol 17;
● Included Decoders – Required if you plan to use the decoder for IP graphing. Select the decoders that include the matched traffic, or choose IP if not sure
● Conflicting Decoders – Required if you plan to use the decoder for IP graphing. Select the decoders that might match same traffic, but not always. The option is used only for displaying stacked decoders inside IP graphs
● Filter Engine – If you intend to use Wanguard Filter for anomalies detected using the decoder, select the most specific Filter engine that could analyze the traffic. Otherwise, select disabled
● Netfilter Expression – Enter Netfilter/iptables argument(s) that match the same traffic also matched by the decoder to prevent irrelevant packets from passing the Netfilter firewall